-
Cloud Based CPA Firms Meet Remote Work Demands in COVID-19 Crisis
The cloud has enabled firms to quickly pivot to a near 100% remote workforce without losing operational efficiency. Many firms nationwide invested in the public cloud (Microsoft Azure) to support…
-
Focusing on Our Clients During COVID-19
With accounting firms in the middle of tax season, and the Coronavirus (COVID-19) pandemic crisis spreading, firms are working to support remote workers as fast as possible. According to Accounting…
-
Coronavirus’s Impact on CPA Firms
Cloud Technology Can Help CPA Firms Adjust to Growing Need to Work Remotely According to the CDC, more than 75 countries have reported confirmed cases of COVID-19, also known as coronavirus. From its origin in Wuhan, China, coronavirus has grown to be a global…
-
Data Protection From the Inside Out
Originally published March 2020 by Bill Sorenson, VP of Strategy FinTech – CISO, Netgain in New Jersey CPA Magazine March/April Edition. Full magazine can be viewed at njcpa.org. Cybersecurity challenges and…
-
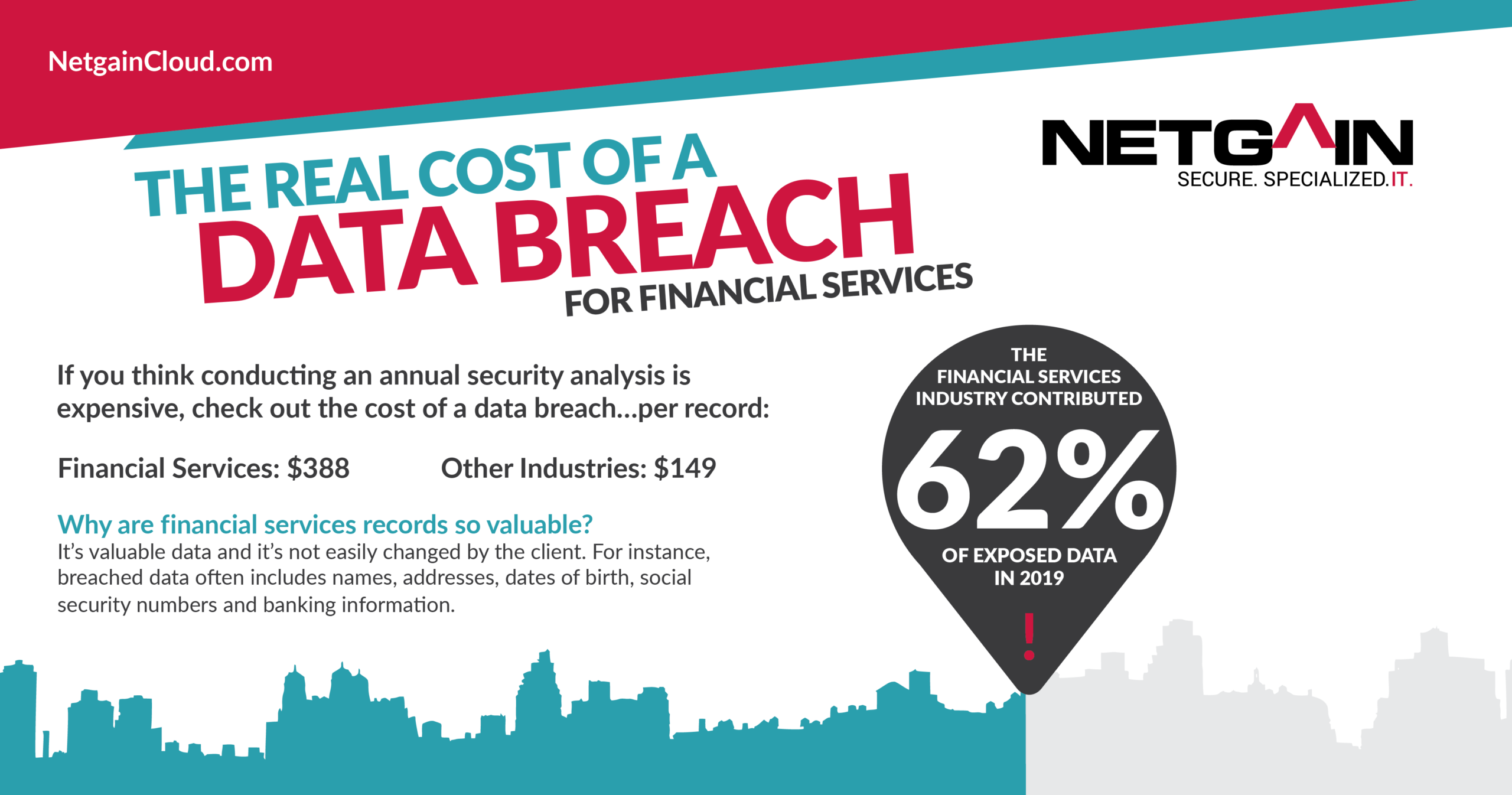
How Costly is a Data Breach?
Just two years ago, we released a blog about the “Real Cost of a Data Breach for Financial Services.” Now, only 24 months later, we’re revisiting the statistics and sharing…
-
2020 Cloud Predictions
When Netgain was founded in 2000, we were considered an “application service provider” or ASP. This was fancy terminology for a service that wasn’t yet market-ready – cloud computing. For…
-
Building Your Cloud Strategy – Selecting the Platform and Working the Plan to Success
Originally published December 17, 2019 by Bill Sorenson, VP of Strategy FinTech – CISO, Netgain at www.boomer.com. The Cloud is Here to Stay Last month we looked at the beginning…
-
Cloud vs. On-Premise Cost Comparison
Forrester Research forecasted that healthcare IT budgets would increase by nearly 9% this year, due to an increasing investment in technology. Similarly, research-giant Gartner agreed with the forecasted growth, but…
-
Building an IT Roadmap
In the 1700’s, Benjamin Franklin had already figured it out: “If you fail to plan, you’re planning to fail.” As each organization should have business plans and goals, organizations of…
-
Building Your Cloud Strategy – Starting at the Beginning
Originally published November 12, 2019 by Bill Sorenson, VP of Strategy FinTech – CISO, Netgain at www.boomer.com. The Cloud is Here to Stay The migration to the cloud is happening…
-
Password Best Practices: What Makes an Effective Password?
The number of passwords the average person has is extensive. Keeping track of all these passwords is a hassle…and then you add in the dreaded password reset day when you…
-
Netgain Joins Hybrid IT Monitoring-Heavyweight LogicMonitor’s Partner Network to Bolster Proactive Monitoring Service
We’re excited to announce that LogicMonitor, an industry leader in hybrid IT monitoring software, has invited Netgain to join its new partner network as a pillar member. LogicMonitor’s software-as-a-service (SaaS) platform…