Search results for: “data”
-

Cybersecurity Awareness Month 2024: Securing Your Business with Advanced Security Solutions
October marks Cybersecurity Awareness Month, an initiative led by the Cybersecurity & Infrastructure Security Agency (CISA) to raise awareness and promote best practices for staying safe online. Now in its…
-

IT Security Demystified
During this webinar, we will demystify the IT security layers required to mitigate risk and improve your firm’s security posture. We will address security for firms housing data and applications…
-

Cloud vs. On-Prem: Why CPA Firms Are Moving to the Cloud
For many CPA firms, IT infrastructure has historically been an afterthought—something managed in-house with minimal investment beyond basic security and compliance needs. But as firms grow, expand services and adopt…
-

Don’t Let Compliance Drive Your Cybersecurity: 7 Key Insights for Healthcare Administrators
Healthcare administrators carry the pivotal duty of protecting patient information as they navigate the complexities of the industry. Compliance often takes the spotlight, but meeting regulations doesn’t guarantee optimal cybersecurity.…
-

Security Lesson #6: What Are Endpoints and How Do You Secure Them?
In our last post, we talked about application security and how the security measures at the application level prevent data or code within the application from being stolen or hijacked.…
-

How CPA Firms Can Protect Themselves from Business Email Compromise
Cybercriminals are increasingly targeting CPA and accounting firms through business email compromise (BEC)—a sophisticated cyberattack that leverages trust and routine processes to exploit financial and sensitive data. Unlike traditional phishing…
-

Three Tips on Why Multi-Factor Authentication is Critical to Data Security
Cybercrime is rife in 2022. Kaspersky released a new report revealing a growing number of cyberattacks on small businesses so far in 2022. Researchers compared the period between January and April 2022…
-
Security Lesson #7: The Essentials of Implementing Effective Perimeter Security
As I highlighted in my first post, no company or government agency is immune to cyberattacks, and these attacks are a growing threat to every organization. To protect against these attacks, you need…
-
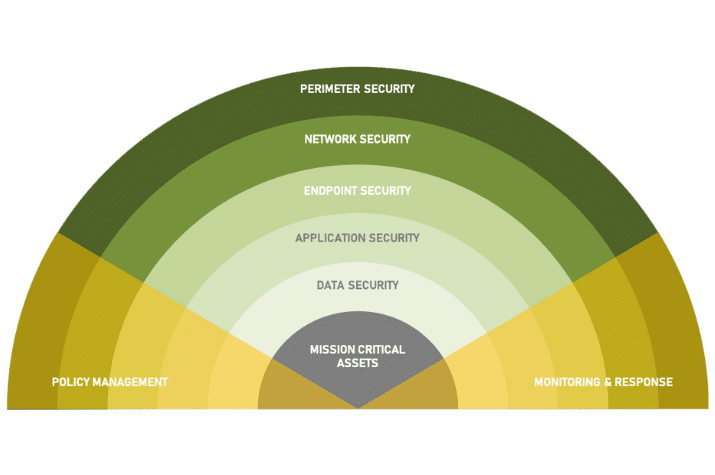
What we learned as a ransomware victim – so you don’t become one
Joining the Ranks of Cyberattack Victims Microsoft. Marriott. Equifax. FireEye. The US Government. Netgain. All of these organizations have one unfortunate common thread: They – we – have all been…
-

Preparing for the Upcoming Tax Season – IRS 4557 Updates
As the busy season approaches, CPA firms are gearing up to manage an influx of client data and tax returns. But while handling this surge in activity, it’s crucial to…
-

Optimizing Azure Spend for Healthcare Providers: Making the Most of Your Budget
Technology is an indispensable component of patient care, data management, and system operations. Healthcare providers are increasingly turning to cloud solutions, with Microsoft Azure emerging as a popular choice. While…
-
Five Insights from Our Experience Using Microsoft 365 Copilot
In its rush to translate GenAI into reality, Microsoft has applied Copilot terminology to practically all its GenAI offering–from Azure to GitHub to Office. This blog focuses squarely on Microsoft…